
The first day of Pwn2Own Automotive 2026 has concluded with security researchers earning $516,500 in rewards for discovering 37 unique zero-day vulnerabilities across a range of modern automotive systems.
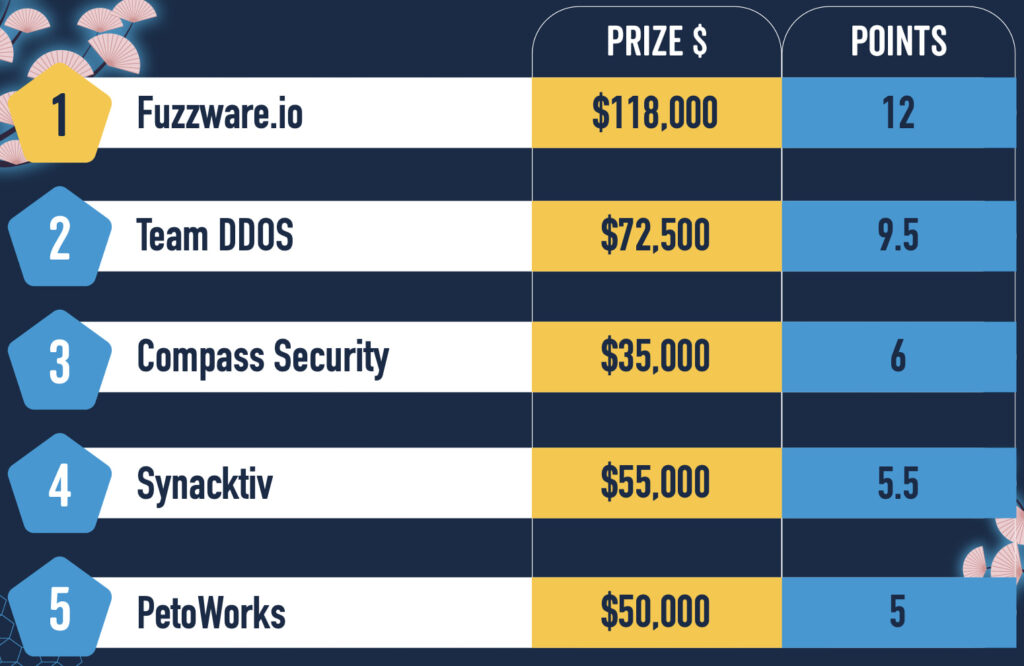
The Munich-based team Fuzzware.io emerged as the early frontrunner in the “Master of Pwn” competition, while Team DDOS remains in close pursuit.
ZDI
The annual Pwn2Own Automotive event, organized by Trend Micro’s Zero Day Initiative (ZDI), is a hacking competition focused on uncovering security flaws in automotive software and hardware. The competition showcases real-world exploit chains targeting infotainment systems, EV chargers, and vehicle connectivity components. This year’s event takes place in Tokyo and includes prominent industry targets from Sony, Tesla, Kenwood, Alpine, ChargePoint, and others.
Among the most notable wins on Day One was Fuzzware.io’s attack on the Autel EV charger, where researchers chained two vulnerabilities to achieve code execution and manipulate the charging signal. This full chain, which included a successful signal manipulation add-on, earned the team $50,000 and 5 Master of Pwn points.
Berlin-based security firm Neodyme AG also made headlines by exploiting a stack-based buffer overflow to gain root access on the Alpine iLX-F511 infotainment unit, earning $20,000. This device, widely used in aftermarket automotive installations, became a frequent target, with multiple teams uncovering vulnerabilities ranging from buffer overflows to improper permissions.

Fuzzware.io maintained its momentum throughout the day, successfully targeting multiple systems. One of the highest bounties went to their exploit against the Alpitronic HYC50 fast charger in Field Mode, where a single out-of-bounds write resulted in a full takeover and a $60,000 prize, the largest single payout of the day.
Other successful teams included Synacktiv, which leveraged an information leak and an out-of-bounds write to compromise a Tesla infotainment unit via USB-based attack vectors. Their effort earned $35,000 and reinforced the growing concerns about physical access vulnerabilities in connected cars.
Team DDOS demonstrated notable prowess in exploiting the ChargePoint Home Flex EV charger, combining two bugs, including command injection. Although their add-on failed, they still secured a $40,000 reward.
Compass Security, SKShieldus, PetoWorks, and Cycraft Technology were among the other groups earning payouts for various exploit chains. In total, more than a dozen vendors were targeted, with vulnerabilities including hardcoded credentials, heap-based overflows, command injections, and authentication bypasses.
Phoenix Contact’s CHARX SEC-3150, a commercial-grade EV charging controller, also drew significant attention. Fuzzware.io, Team Zeroshi, and 78ResearchLab all found critical flaws, including race conditions and denial-of-service bugs, that could disrupt power delivery or grant persistent control.
Pwn2Own’s rules award reduced payouts and points for duplicate or previously disclosed vulnerabilities, referred to as “collisions.” Several teams encountered these, particularly against well-targeted devices such as the Alpine iLX-F511 and the Kenwood DNR1007XR.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


