Cyble researchers have identified a new NFC relay attack campaign targeting users in Brazil.
Dubbed “RelayNFC,” Cyble Research and Intelligence Labs (CRIL) researchers identified five phishing sites distributing the malicious app, which claims to secure payment cards. The malicious application captures the victim’s card details and relays them to attackers for fraudulent transactions.
The malware is also highly evasive and remains undetected by security tools.
NFC Relay Attack App Evades Security Tools
RelayNFC is a “lightweight yet highly evasive malware” because of its Hermes-compiled payload, Cyble said. Use of the JavaScript engine “makes detection significantly harder, enabling it to stealthily capture victims’ card data and relay it in real time to an attacker-controlled server,” the researchers said.
VirusTotal detections of the NFC relay attack malware were at zero at publication time, “indicating very low visibility across the security ecosystem, and the code suggests a high likelihood of continued development,” they said.
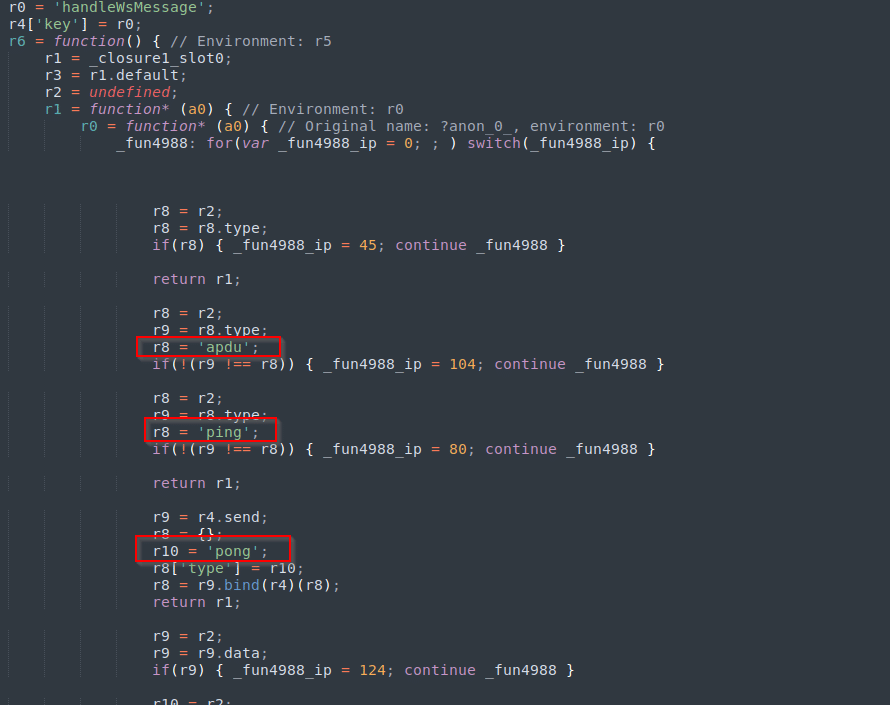
RelayNFC uses a full real-time Application Protocol Data Unit (APDU) relay channel that enables attackers to complete transactions “as though the victim’s card were physically present.”
The researchers also identified a related variant that attempts to implement Host Card Emulation (HCE), suggesting that the threat actor is exploring other NFC relay techniques too.
Other malware strains exploiting Near-Field Communication (NFC) capabilities to intercept or relay contactless payment data have included Ngate, SuperCardX, and PhantomCard, suggesting a growing trend of NFC exploits, Cyble said.
RelayNFC Malware Relies on Phishing Sites
Distribution of RelayNFC relies entirely on phishing, tricking users into downloading the malware. The campaign uses a Portuguese-language page that prompts victims to install the malicious payment card security app (image below).


The researchers identified five malicious sites distributing the app, “indicating a coordinated and ongoing operation targeting Brazilian users.” Those sites include:
- maisseguraca[.]site
- proseguro[.]site
- test[.]ikotech[.]online
- maisseguro[.]site
- maisprotecao[.]site
RelayNFC appears to be a new variant built using the React Native framework and has been active for at least a month. The malware operates as a “reader,” the researchers said, capturing victim card data and relaying it to the attacker’s server. After installation, the app immediately displays a phishing screen that tells the user to tap their payment card on the device.
Once the card data has been read, RelayNFC displays another phishing screen that prompts the victim to enter their 4- or 6-digit PIN.
APDU Commands Turn Device Into ‘Remote NFC Reader’
The RelayNFC code is built around a relay channel that uses a persistent WebSocket connection to forward Application Protocol Data Unit (APDU) commands between the attacker’s server and the victim’s NFC subsystem, “effectively turning the infected device into a remote NFC ‘reader’ for the attacker,” the researchers said.
The NFC controller processes the command and generates a genuine APDU response, as the card would during a legitimate transaction. RelayNFC captures that output and returns it to the command-and-control server in an “apdu-resp” message, “preserving the original request ID and session ID so the attacker’s device can continue the EMV transaction seamlessly.”
“This real-time, bidirectional relay of APDU commands and responses is what enables the attacker to execute a full payment flow remotely, as if the victim’s card were physically present at their POS terminal,” the researchers said.
“By combining phishing-driven distribution, React Native–based obfuscation, and real-time APDU relaying over WebSockets, the threat actors have created a highly effective mechanism for remote EMV transaction fraud,” they said.
The researchers said their findings underscore the need for strong device-level protections, user awareness, and monitoring by financial institutions.