
A newly discovered Android spyware family named LANDFALL has been uncovered by researchers at Unit 42, revealing an advanced, targeted surveillance campaign against Samsung Galaxy smartphones.
The operation leveraged a critical zero-day vulnerability (CVE-2025-21042) in Samsung’s image processing library, using maliciously crafted image files sent through WhatsApp to execute silent, zero-click attacks.
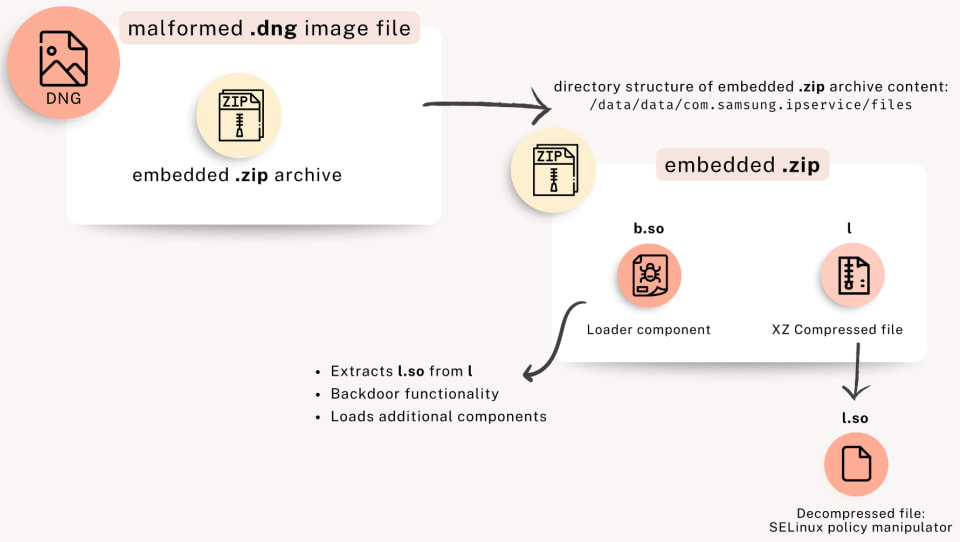
The discovery of LANDFALL traces back to a broader investigation by Palo Alto Networks’ Unit 42 in mid-2025, following disclosures about zero-day exploit chains targeting iOS and WhatsApp. While searching for related indicators on Android, researchers found several malformed DNG image files uploaded to VirusTotal between July 2024 and February 2025. These images contained embedded ZIP archives that delivered the LANDFALL spyware payloads, designed specifically for Samsung Galaxy devices.
At the core of the exploit was a flaw in Samsung’s proprietary libimagecodec.quram.so library, patched in April 2025. The vulnerability (CVE-2025-21042) allowed remote attackers to execute code on target devices through specially crafted DNG images. Despite its patch, the exploit had been active for months before its disclosure.
LANDFALL exhibits traits of commercial-grade surveillance tools and has been linked to activity in the Middle East. The spyware offers a modular architecture capable of wide-ranging espionage, including microphone recording, call and SMS interception, photo collection, and device fingerprinting. Its loader (b.so) and a second component (l.so) embedded within the DNG images manipulate the SELinux policy to maintain persistence and elevate privileges.
Samsung, one of the largest smartphone manufacturers globally, dominates the Android market with its Galaxy line, including the S22, S23, S24, and Z Fold series, all of which were specifically targeted by LANDFALL.
The malicious campaign delivered LANDFALL via image files disguised as WhatsApp media, using filenames like IMG-20240723-WA0000.jpg and WhatsApp Image 2025-02-10 at 4.54.17 PM.jpeg. Once opened or processed by the system, the images triggered the exploit chain, initiating a multi-stage infection process. Unit 42 noted similarities between LANDFALL’s tactics and a broader pattern of mobile spyware attacks involving DNG image vulnerabilities across iOS and Android.
The infection chain centers on two main components:
- b.so (Bridge Head): A stripped ARM64 ELF binary acting as the primary loader and command handler. It facilitates data collection, code injection, and command execution.
- l.so: A SELinux policy manipulator extracted from an XZ-compressed file, enabling privilege escalation and stealthy persistence mechanisms.
The loader communicates with command-and-control (C2) servers over HTTPS on non-standard ports, initially pinging the servers before sending encrypted POST requests. The C2 configuration is embedded in an encrypted JSON object within the malware binary, and contains identifiers, network settings, and encryption keys. Six C2 domains were identified, some of which were flagged as malicious by Turkish CERT authorities.
Unit42
While Unit 42 did not attribute the spyware to a specific actor, they identified tradecraft overlaps with known private-sector offensive actors (PSOAs), including Variston and potentially Stealth Falcon. Debug strings within the loader used the term “Bridge Head,” a term also found in known commercial spyware frameworks such as Heliconica, tied to PSOAs operating out of the UAE.
Samsung users should ensure their devices are updated to the latest firmware version and consider disabling automatic media downloading in messaging apps like WhatsApp to prevent the execution of zero-click exploits.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


