
A previously undocumented Android firmware backdoor named Keenadu has been discovered, embedded directly into system components of multiple tablet brands.
Kaspersky researchers say the malware grants attackers near-total control over infected devices and reveals operational links with Triada, BADBOX, and Vo1d.
The investigation began after the company’s earlier discovery of Triada infections in counterfeit Android devices. While searching for similar firmware-level threats, Kaspersky analysts identified Keenadu operating in a comparable manner, deeply integrated into the operating system and capable of infecting every app launched on a device.
Embedded in firmware at build time
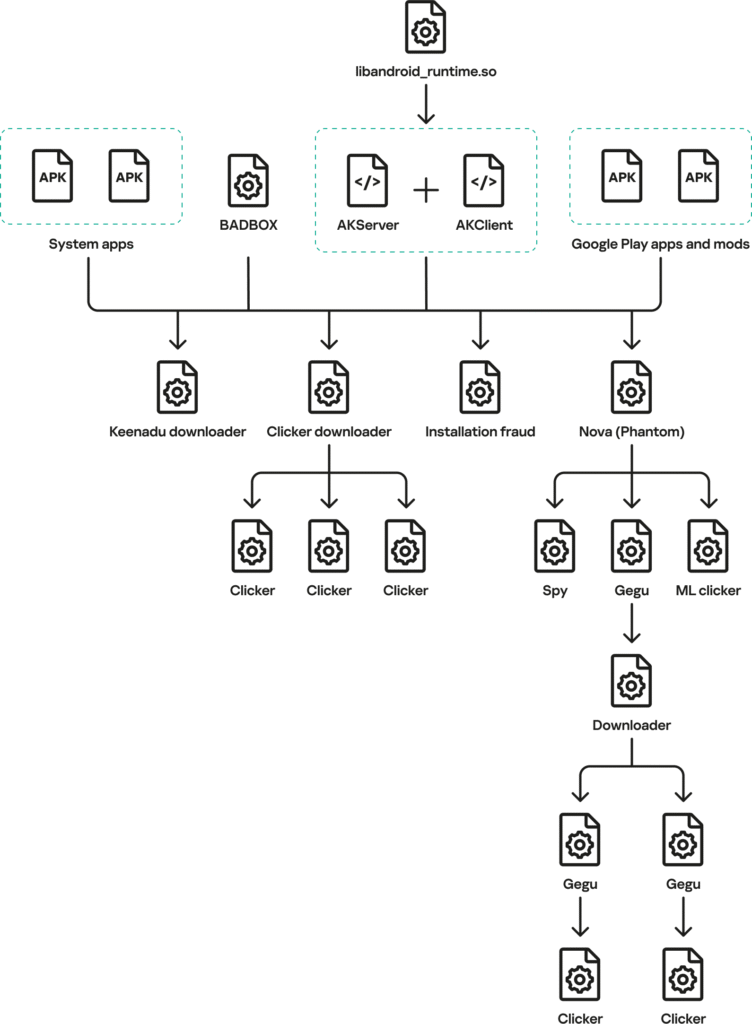
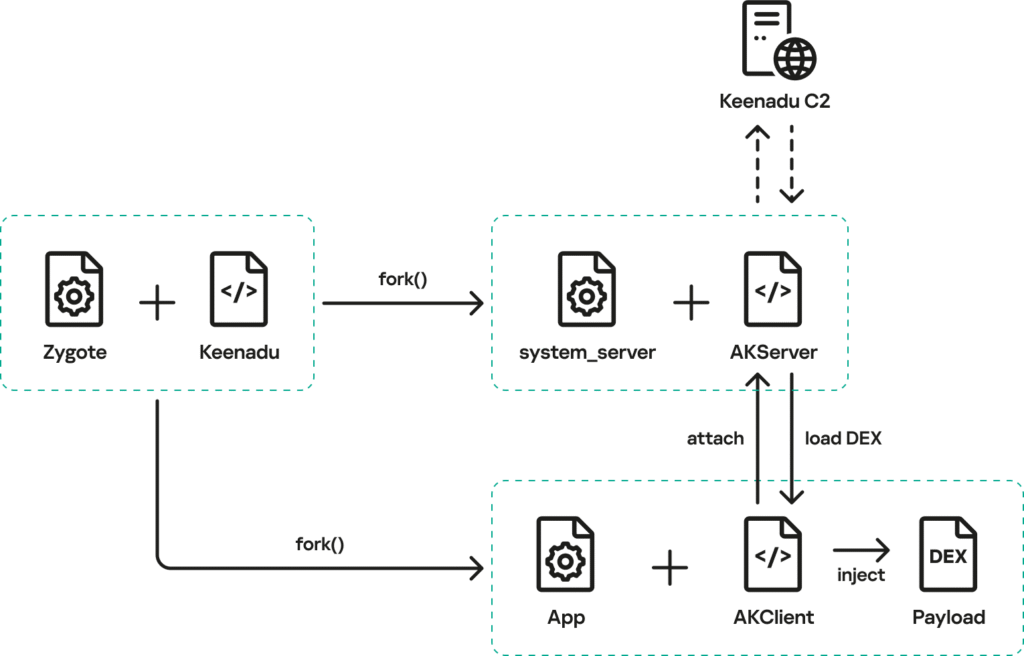
Unlike typical Android malware delivered through malicious apps, Keenadu is integrated directly into the device firmware. According to Kaspersky, the malicious code was inserted during the firmware build process, likely as part of a supply chain compromise. The attackers modified a core Android library that is loaded by every app, ensuring the backdoor runs inside all applications on the device.
Once active, Keenadu injects itself into Android’s Zygote process, the system component responsible for launching apps, allowing it to silently operate across the entire device. This approach effectively bypasses Android’s app sandbox protections and enables the malware to circumvent normal permission controls.
Kaspersky traced infections to firmware images for several tablet models, including Alldocube devices. Even firmware versions released after the vendor acknowledged that malware issues had been found were found to contain the backdoor. Because the affected firmware images were digitally signed, researchers believe the compromise occurred during development rather than through a hacked update server.
Telemetry data shows that Keenadu infections were identified in tablets from multiple manufacturers, indicating a broader supply chain issue. Kaspersky says it has notified the affected vendors.
Kaspersky
A modular malware platform
Keenadu acts as a multi-stage loader. After activating, it contacts attacker-controlled servers, encrypting communications and exchanging device information such as model, operating system version, and unique identifiers. The malware delays the download of additional payloads for weeks to evade security analysis.
The downloaded modules are tailored to specific apps and purposes. Kaspersky observed plugins targeting popular apps such as Google Chrome, YouTube, Facebook, Amazon, and Temu, as well as system launcher components.
Kaspersky
One module hijacks Chrome browser searches, intercepting queries entered in the address bar and redirecting them to alternative search engines controlled by the attackers. Others interact with advertising elements on websites to generate fraudulent ad revenue. A separate component monitors app installations and simulates ad clicks to fraudulently monetize downloads.
Although much of the observed activity centers on advertising fraud, researchers also identified modules capable of stealing account credentials from messaging and social media apps, including Telegram and Instagram. Code for stealing WhatsApp credentials was present but not actively used.
Kaspersky
Connections to major Android botnets
The researchers found overlaps in infrastructure and similarities in code between Keenadu and the BADBOX botnet. In some cases, BADBOX components were used to deploy Keenadu modules. Kaspersky also uncovered evidence that earlier campaigns involving Triada and modified WhatsApp applications may have been joint operations involving multiple malware families.
While not all relationships are directly confirmed, the investigation establishes clear ties between Keenadu, BADBOX, Triada, and the Vo1d botnet. This suggests that major Android malware operators may share infrastructure or tooling, or collaborate on certain campaigns.
Kaspersky reports that 13,715 users worldwide have encountered Keenadu or its modules. The highest number of detections occurred in Russia, Japan, Germany, Brazil, and the Netherlands.
Removal is difficult
Because Keenadu is embedded in a core system library stored on Android’s read-only system partition, it cannot be removed like a typical malicious app. Attempting to manually delete infected components could render a device unusable.
Kaspersky recommends that affected users:
- Check for official firmware updates from the device manufacturer.
- Install updates only from trusted sources.
- Use reputable mobile security software to scan devices.
- Avoid using devices that remain infected if no clean firmware is available.
- Uninstall any detected malicious third-party apps.
The researchers warn that while Keenadu is currently focused largely on ad fraud and monetization schemes, its deep system access enables attackers to steal credentials, spy on users, or deploy additional malware at any time.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


