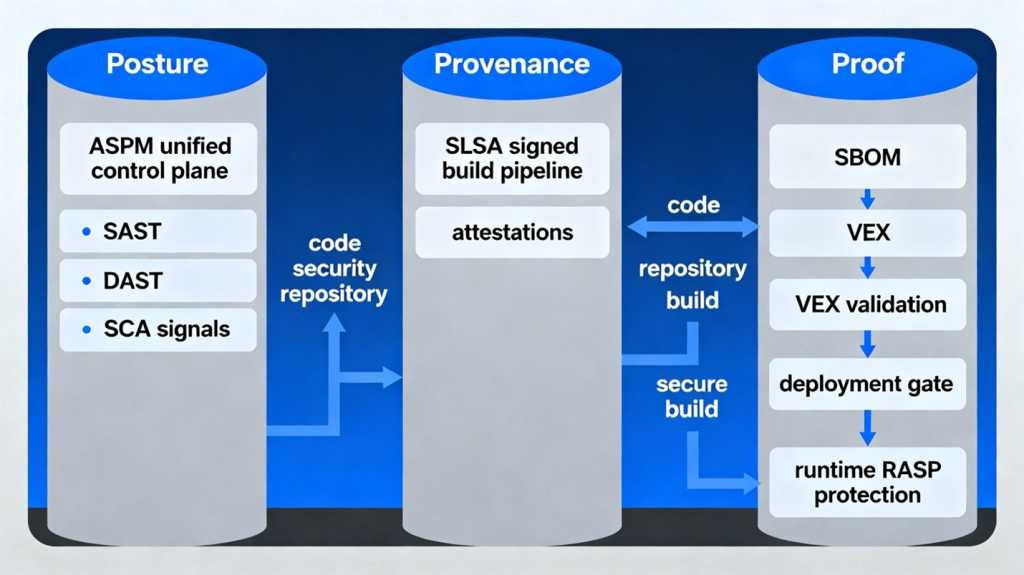
I have stared at enough scanner dashboards to recognize the pattern. SAST flags theoretical flaws that never execute. DAST shrugs because the route to the vulnerable function is blocked. SCA floods the zone with CVEs that never touch a hot path. MAST scolds my mobile app for secrets I retired last quarter. These tools are still essential, yet they now form a baseline rather than a destination. The next chapter is not another “silver bullet” product; it is a shift toward posture, provenance and proof.
Sunil Gentyala
Over the past year the community has admitted the obvious: the battleground is the software supply chain and the running system, not only pre‑release scans. OWASP’s 2025 update elevated software supply chain failures to A03, reframing vulnerable and outdated components as a systemic ecosystem risk that spans dependencies, build systems and distribution infrastructure (Endor Labs overview here). In parallel, CISA pushed SBOM guidance forward with a 2025 draft that demands richer, machine‑readable metadata and emphasizes automation for scale.
Posture, provenance and proof: The new trinity
Application security posture management (ASPM) is the control plane that makes the old quartet useful again. Gartner’s 2025 Innovation Insight described how ASPM connects scattered signals across the SDLC, enforces policy and prioritizes based on context, such as reachability and exposure in practice, which means pulling SAST, DAST, SCA, IaC and runtime findings into a single view, then filtering for the small subset that really matters.


