editorially independent. We may make money when you click on links
to our partners.
Learn More
Phishing is no longer the sloppy fake login page scam teams have trained for — it’s a polished, commercialized industry built to steal sessions, defeat multi-factor authentication (MFA), and automate account takeovers at scale.
Flare researchers recently analyzed the phishing kit economy in the cybercrime underworld.
“While working on this research, I came to a clear realization: the odds were never really in our favor. Attackers have always exploited human psychology. Technology didn’t invent social engineering; it scaled it,” said Assaf Morag, cybersecurity researcher at Flare in an email to eSecurityPlanet.
He added, “Automation, refined UI and UX patterns, and now AI has turned manipulation into an efficient, industrial process.”
Assaf explained, “Humans, meanwhile, haven’t changed. That’s why phishing and social engineering need to be treated as systemic risks, and addressed through education and security design that accepts human vulnerability as a given.”
Inside the Phishing-as-a-Service Economy
Flare analyzed 8,627 posts across messaging platforms, open sources, deep web forums, and dark web spaces tied to phishing kits and real-time phishing activity
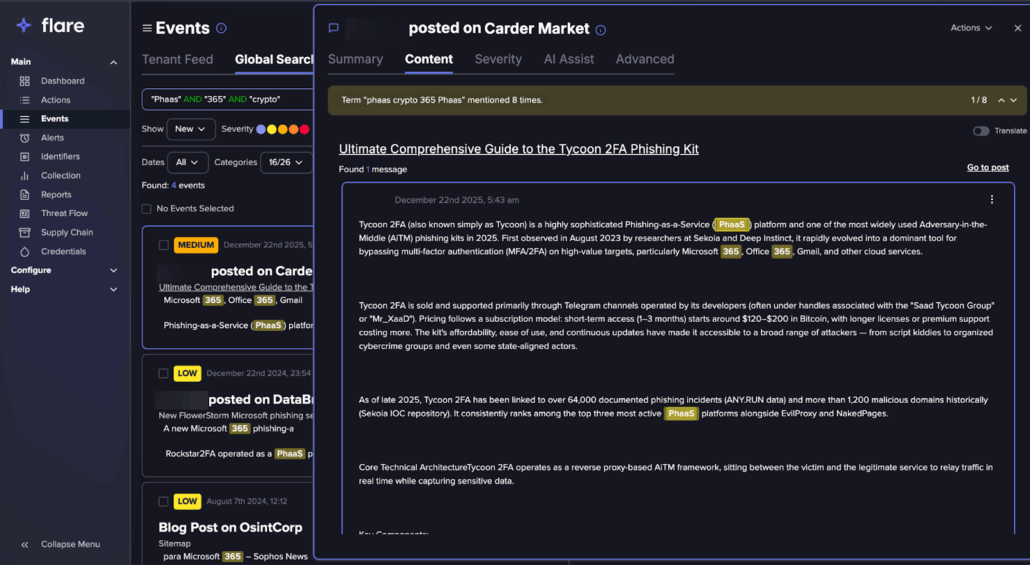
The dataset shows phishing kits operating like legitimate SaaS: packaged tooling, documentation, updates, customer support, and subscription-style access via phishing-as-a-service (PhaaS).
Instead of building from scratch, an operator can upload a kit, set basic exfiltration options, and launch a campaign — often with features like bot filtering, dynamic branding, Telegram-based data theft, and victim dashboards.
The market has shifted toward adversary-in-the-middle (AiTM) and reverse-proxy platforms, including widely discussed kits like EvilProxy and Tycoon2FA, which are designed to steal authenticated sessions — not just credentials.
This matters because it undercuts a defensive assumption that “MFA will stop the damage even if a password leaks.”
How Reverse-Proxy Phishing Works
At a high level, reverse-proxy phishing places the attacker between the user and the real login service.
The victim believes they are logging in normally, but the proxy relays traffic to the legitimate site while quietly capturing authentication artifacts — often session cookies and tokens that can be replayed to take over the account.
This means a user can successfully authenticate and still hand the attacker everything needed to bypass MFA.
The report also highlights how scale is achieved through “combo kits” — multi-brand phishing panels that impersonate many services in one deployment.
In Flare’s analysis, 43.83% of entries referenced multi-target lures, consistent with panels that let attackers rotate brands and victim paths quickly.
These kits function like a fraud toolkit: one package, many targets, many ways to monetize.
Patterns in target selection reinforce the economics.
Single-target campaigns in the dataset heavily favored crypto and Microsoft/O365, aligning with quick cash-out and repeatable enterprise access.
Multi-target kits, meanwhile, clustered around banking, e-commerce, and PayPal — a reliable “fraud trifecta” for consumer monetization at scale.
Defending Against AiTM Phishing
As phishing attacks evolve into session hijacking and token theft, organizations need defenses that go beyond basic MFA and traditional email filtering.
Modern identity-based threats — especially AI-assisted and adversary-in-the-middle (AiTM) techniques — can bypass older controls and compromise accounts in minutes.
- Adopt phishing-resistant authentication by prioritizing FIDO2 security keys or passkeys over OTP-based MFA for high-risk users and critical systems.
- Strengthen conditional access with device trust requirements, shorter session lifetimes, and risk-based step-up authentication to limit token replay and unauthorized access.
- Expand detection for AiTM phishing and session hijacking by monitoring anomalous login flows, suspicious hosting infrastructure, and signs of token reuse or unusual session behavior.
- Harden email and web controls by enforcing DMARC/SPF/DKIM, using time-of-click URL inspection, and filtering QR code and attachment-based phishing payloads.
- Reduce account takeover persistence by restricting OAuth app consent, requiring admin approval for high-risk permissions, and monitoring for suspicious token grants or new third-party apps.
- Contain compromises faster by automating incident response actions such as token revocation, forced re-authentication, credential resets, and mailbox rule or forwarding cleanup.
- Limit blast radius through least privilege, privileged access separation, and tighter segmentation of sensitive SaaS, admin portals, and financial systems.
Together, these steps help contain compromises and reduce the blast radius across critical systems.
MFA Bypass Is the New Normal
Phishing has matured into a service economy where MFA bypass is increasingly built into the business model, and that reality forces defenders to rethink long-held assumptions about identity security.
When attackers can steal sessions instead of just passwords, preventing compromise becomes harder — but limiting impact becomes even more important.
Organizations that adopt phishing-resistant authentication, stricter conditional access, and automated containment can help prevent one hijacked session from becoming an enterprise-wide breach.
To further contain identity-based threats, many organizations are now adopting zero-trust solutions that verify every access request and minimize implicit trust.