editorially independent. We may make money when you click on links
to our partners.
Learn More
A vulnerability in Apache Tomcat enables users to bypass certain access controls by leveraging legacy HTTP/0.9 requests.
Under specific configurations, the issue could allow attackers to circumvent defined security constraints.
“If a security constraint was configured to allow HEAD requests to a URI but deny GET requests, the user could bypass that constraint on GET requests by sending a (specification invalid) HEAD request using HTTP/0.9,” said Apache in its advisory.
Breaking Down the Tomcat Access Control Flaw
Tracked as CVE-2026-24733, the issue is rated low severity but affects multiple supported Apache Tomcat branches as well as older, end-of-life (EOL) releases.
The root cause stems from Tomcat’s handling of HTTP/0.9, an obsolete version of the protocol that predates modern HTTP method validation and header standards.
Under typical HTTP/1.1 or HTTP/2 operation, administrators can define security constraints that allow certain methods — such as HEAD — while explicitly denying others, such as GET, for a specific URI.
These constraints are commonly used to restrict access to resource bodies while permitting limited metadata checks.
CVE-2026-24733 introduces an enforcement gap under a specific set of conditions:
- A security constraint is configured to allow HEAD requests.
- The same constraint denies GET requests.
- An attacker sends a malformed HEAD request using HTTP/0.9 semantics.
Because Tomcat did not limit HTTP/0.9 traffic to GET-only handling, its method parsing logic could process the request in a way that bypasses the intended GET restriction.
In effect, content that should have been blocked may become accessible under these narrowly defined circumstances.
The following versions are affected:
- Apache Tomcat 11.0.0-M1 to 11.0.14
- Apache Tomcat 10.1.0-M1 to 10.1.49
- Apache Tomcat 9.0.0.M1 to 9.0.112
- Older, unsupported versions are also affected and should be upgraded to a supported branch.
The vulnerability does not enable authentication bypass, privilege escalation, or remote code execution.
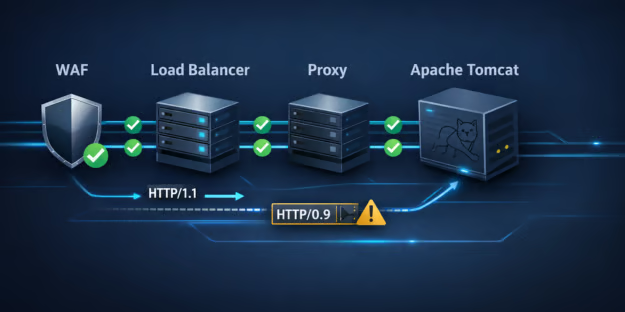
Exploitation is configuration-dependent and requires that HTTP/0.9 traffic be accepted end-to-end by the deployment stack.
In many modern architectures, reverse proxies, load balancers, API gateways, or web application firewalls (WAFs) normalize or reject legacy protocol variants before they reach Tomcat.
However, atypical proxy chains, legacy integrations, or custom clients may not provide that protection.
At the time of publication, Apache reported no evidence of active exploitation in the wild.
Reducing Tomcat Access Control Risk
Although CVE-2026-24733 is rated low severity, it provides a practical reason to review patch management processes and access-control configurations.
Legacy protocol handling and method-specific rules can create subtle enforcement gaps if they are not regularly tested and validated.
- Patch to the latest supported version of Apache Tomcat and validate the update through testing to ensure the vulnerability is fully remediated.
- Review and validate security constraint configurations, especially where HEAD is allowed and GET is denied, to confirm enforcement aligns with intent.
- Enforce strict protocol validation at the edge by configuring reverse proxies, load balancers, or WAFs to reject or normalize HTTP/0.9 traffic.
- Implement HTTP method allowlisting at multiple layers to block unnecessary or unexpected request methods before they reach Tomcat.
- Harden Tomcat connector and server configurations while restricting direct internet exposure through proper network segmentation.
- Enable logging and monitoring to detect malformed requests, protocol downgrades, or anomalous HTTP method usage that may indicate probing attempts.
- Leverage vulnerability management tools and regularly test incident response plans to ensure teams can detect, investigate, and contain access control bypass scenarios.
These measures help limit the blast radius of potential access control bypasses while strengthening long-term resilience across the application stack.
Managing Legacy Protocol Risk
Although CVE-2026-24733 is limited in scope and there are no reports of active exploitation, it serves as a reminder that legacy protocol support and specific configuration choices can create subtle gaps in access control.
Organizations running Tomcat in production should focus on applying updates, reviewing constraint configurations, and ensuring consistent protocol handling across their environments.
Even lower-severity issues can introduce unnecessary exposure when combined with outdated software or untested settings.
This type of access-control risk underscores the broader value of zero-trust solutions, which are designed to enforce continuous verification and minimize implicit trust across application environments.