
Jamf Threat Labs has published a technical analysis detailing how the commercial Predator spyware disables Apple’s iOS camera and microphone recording indicators after a device has already been compromised.
The report shows that Predator uses a single, carefully placed hook to suppress both visual alerts, allowing covert surveillance to continue without triggering the green or orange status bar dots in iOS.
Apple introduced recording indicators in 2020 as part of iOS 14, displaying a green dot when the camera (and possibly microphone) is in use and an orange dot when only the microphone is active. These indicators are handled by SpringBoard, the core iOS process responsible for the home screen and system UI, through private framework classes that track sensor activity. Legitimate apps cannot suppress these alerts.

Jamf
Predator bypasses this protection by targeting the internal class SBSensorActivityDataProvider, specifically the _handleNewDomainData: method. This method is invoked whenever the sensor state changes, such as when the camera or microphone is activated. By installing a hook on this single method inside SpringBoard, Predator intercepts sensor activity updates before they reach the UI layer.
The suppression mechanism relies on a subtle abuse of Objective-C behavior. On ARM64 systems, the self pointer is passed in register x0 during method invocation. Predator’s hook modifies the thread state so that x0 is set to NULL before _handleNewDomainData: executes. In Objective-C, sending a message to nil results in a no-op; no code is executed, and no error is raised. As a result, the sensor update is silently dropped, and the recording indicator never appears.
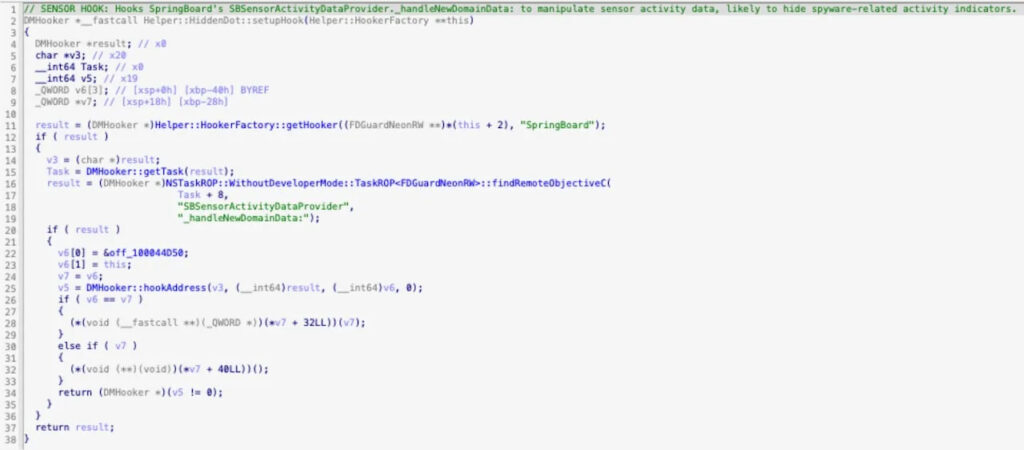
Jamf
At the assembly level, this manipulation boils down to a single STR XZR instruction that zeroes out the relevant register in the thread state. The hook returns a value of 2 to the underlying DMHooker framework, instructing it to continue execution with the modified register state. According to Jamf, a single hook is sufficient to suppress both camera and microphone indicators, as SBSensorActivityDataProvider aggregates all sensor activity before forwarding it to the UI.
The researchers also uncovered abandoned development code referencing SBRecordingIndicatorManager, suggesting that earlier versions of Predator may have attempted to manipulate the UI layer directly. That approach would have required multiple hooks and risked race conditions. The final implementation, which blocks sensor data at the source, is cleaner and more resilient.
Predator’s modular design extends beyond indicator suppression. A component dubbed “CameraEnabler” uses ARM64 instruction pattern matching to locate internal, non-exported functions within CMCapture.framework. Instead of relying on symbol names, it searches for specific prologue instruction sequences near FigVideoCaptureSourceCreateWithSourceInfo. The hook callback then uses Pointer Authentication Code (PAC) redirection to bypass camera access checks, returning a pre-signed address from a PAC cache to maintain execution flow.
Another module focuses on VoIP interception, hooking AudioConverterNew and AudioConverterConvertComplexBuffer+52 within mediaserverd. It processes audio buffers, converts float32 PCM to int16 using NEON SIMD instructions, downmixes multi-channel audio, and writes captured data using ExtAudioFileWrite(). This module does not include its own indicator-suppression logic, meaning operators must first activate the “HiddenDot” component to avoid visible alerts.
Predator’s approach demonstrates a high level of post-exploitation sophistication, combining Objective-C runtime quirks, ARM64 internals, and PAC-aware redirection to evade built-in privacy safeguards. While no new iOS vulnerability is disclosed, the findings provide defenders with concrete indicators of compromise.
iPhone users should upgrade to the latest iOS version, and those at high risk of being targeted by mercenary spyware should consider enabling Lockdown Mode, which aggressively reduces the attack surface.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


