editorially independent. We may make money when you click on links
to our partners.
Learn More
Flare researchers have identified a threat actor known as TeamPCP behind a large-scale campaign targeting cloud-native infrastructure by abusing exposed orchestration and management interfaces.
First observed in late 2025, the activity reflects a broader shift away from endpoint-focused attacks toward systematic exploitation of cloud control planes.
“The campaign reflects a dark mirror of legitimate markets. Just as modern businesses can scale from a single individual empowered by AI and automation, financially motivated threat actors are adopting similar operating models,” said Assaf Morag, cybersecurity researcher at Flare in an email to eSecurityPlanet.
He added, “Leveraging AI, they combine newly disclosed vulnerabilities (react2shell) with long-standing initial access methods rooted in cloud-native misconfigurations and rapidly convert compromised access into products traded across underground markets.”
Inside the TeamPCP Campaign
The TeamPCP campaign demonstrates how misconfigured cloud services can be transformed into self-propagating attack platforms.
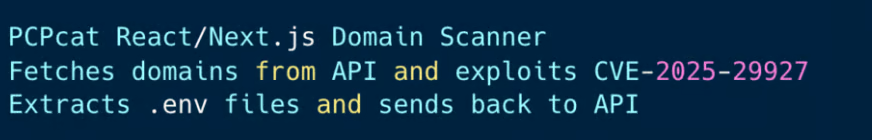
Instead of relying on phishing or zero-day exploits, the group systematically targets exposed Docker APIs, Kubernetes clusters, Ray dashboards, Redis servers, and web applications vulnerable to CVE-2025-29927.
Once initial access is obtained, compromised workloads are repurposed into scanners, proxy nodes, cryptomining infrastructure, and data exfiltration points, allowing the operation to expand rapidly.
Researchers observed the group’s first identified operation — tracked as the PCPcat campaign — peaking around Dec. 25, 2025.
At least 185 servers were confirmed compromised during this phase, with additional indicators suggesting the true scope of exposure extended well beyond those observed hosts.
The timing and scale of the activity point to a coordinated and automated campaign rather than isolated opportunistic exploitation.
At the core of TeamPCP’s attack chain is a high degree of automation built on well-known techniques rather than novel malware.
The group exploits unauthenticated or weakly protected cloud control planes to deploy standardized payloads, most notably a shell script known as proxy.sh.
This script installs tunneling and proxy utilities, deploys additional scanning components, and establishes persistence by registering system services, effectively turning each compromised server into an active participant in the broader operation.
When the malware detects a Kubernetes environment, it follows a cluster-specific execution path by deploying a secondary payload, kube.py.
This component enumerates pods and namespaces, executes commands across accessible workloads, and installs a privileged DaemonSet that enables persistent, cluster-wide control.
As a result, a single foothold can be leveraged to convert an entire Kubernetes cluster into a distributed botnet used for scanning and further exploitation.
TeamPCP also exploits React2Shell vulnerabilities in React and Next.js applications to gain remote code execution, harvest credentials and sensitive data, and deploy follow-on payloads for continued access.
Reducing Risk in Cloud Environments
Campaigns like TeamPCP show how quickly misconfigured cloud environments can be abused when control planes are exposed or insufficiently monitored.
Because these attacks rely on automation and lateral movement rather than novel exploits, effective defense requires a layered, cloud-native approach.
- Harden cloud control planes by restricting access to Docker, Kubernetes, Redis, and Ray APIs through authentication, network segmentation, and firewall controls.
- Enforce least-privilege access across cloud identities, service accounts, and CI/CD pipelines, and prevent secrets from being embedded in images or environment files.
- Limit lateral movement and blast radius by segmenting cloud environments and applying strict admission and runtime policies for containers and workloads.
- Monitor control-plane activity, runtime behavior, and outbound network traffic to detect unauthorized deployments, scanning, cryptomining, and command-and-control activity.
- Strengthen container supply chain security by enforcing image signing, trusted registries, and continuous scanning of images and infrastructure-as-code.
- Proactively identify exposure by continuously scanning cloud environments for publicly accessible orchestration interfaces and misconfigured services.
- Test and refine incident response plans through regular tabletop exercises to ensure rapid isolation, credential rotation, and environment rebuilds after control-plane compromise.
Collectively, these measures help reduce risk from control-plane–focused attacks.
The TeamPCP campaign shows how cloud-focused threats increasingly rely on scale, automation, and common misconfigurations rather than novel malware.
As exposed control planes remain a frequent entry point, organizations benefit from prioritizing continuous visibility, strong access controls, and well-practiced response processes across cloud environments.
To address these risks, security teams are turning to zero-trust solutions that limit access by default and continuously validate activity across control planes.