
A newly published white-box security audit of Mullvad’s account and payment backend services found no high- or critical-severity issues, and auditors confirmed that user privacy and data confidentiality remain intact.
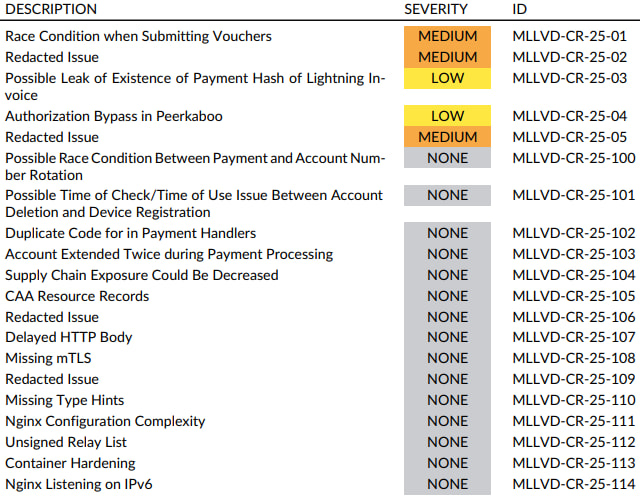
The audit, conducted by German security firm X41 D-Sec in late 2025, uncovered five security-relevant findings, three medium-severity and two low-severity, alongside a set of informational notes focused on defense-in-depth improvements.
The assessment, conducted between October 13 and October 31, 2025, targeted Mullvad’s public-facing API and backend systems for authentication, device registration, payment processing, and WireGuard key distribution. These services are central to Mullvad VPN AB’s infrastructure, a Swedish privacy-focused VPN provider known for its minimal data retention and strong user anonymity guarantees.
X41
The most notable vulnerability uncovered was a race condition in the voucher redemption process that could allow a single voucher to be applied to multiple user accounts. This billing-related flaw was successfully exploited by X41 to redeem a voucher across 16 different accounts during testing. While the issue did not expose user data, it highlighted a need for improved concurrency control in the system’s business logic. Mullvad promptly mitigated the flaw by implementing row-level locking in the database using select_for_update().
Two other medium-severity issues, redacted from the public report, involve denial-of-service vectors that could affect the API’s availability. Though details were withheld to prevent abuse, X41 emphasized that these findings do not compromise data confidentiality or integrity.
Among the low-severity issues, one concerned a potential side-channel that could leak the existence of Lightning Network payment hashes via timing discrepancies during lookup operations. Another allowed for an authorization bypass in the internal “Peerkaboo” service if an attacker possessed relay credentials and manipulated certain HTTP headers. Both issues were addressed during the audit.
The report also includes 15 informational notes that, while not directly exploitable, point to areas where Mullvad could enhance its security posture. These include:
- Strengthening mutual TLS (mTLS) enforcement between internal services.
- Simplifying the Nginx configuration to reduce complexity and the risk of misconfiguration.
- Cryptographically sign the list of VPN relays to prevent relay spoofing.
- Hardening containerized environments by removing unnecessary privileges and restricting internet access.
- Addressing potential concurrency issues that could arise during account number rotations or payment handling.
The audit builds on a similar assessment performed in 2023 and reaffirms the integrity of Mullvad’s API architecture. X41 praised Mullvad’s minimalist data handling approach, emphasizing that the design ensures components such as VPN relays, the API, and associated services operate with strict data compartmentalization. For example, relays are only aware of authorized WireGuard keys, not the identities of the users associated with those keys, and clients rotate those keys regularly.
X41 concluded that Mullvad’s systems compare favorably in security maturity to other software of similar complexity. However, it recommended further improvements in code maintainability and transaction safety, particularly to better manage concurrency in a multi-threaded environment.
CyberInsider would like to remind readers that, while security audits offer valuable insight into a system’s robustness, they represent a snapshot in time. Even thorough, well-executed audits cannot guarantee the complete absence of vulnerabilities or future exploits. They are best viewed as indicators of a project’s security maturity and ongoing commitment to hardening.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


