
A joint investigation by RESIDENT.NGO and Reporters Without Borders (RSF) has exposed a state-sponsored Android spyware campaign run by the Belarusian KGB.
The surveillance tool, dubbed ResidentBat, is physically implanted onto devices during detentions, turning smartphones into powerful tools of repression. The malware, in use since at least 2021, targets journalists and civil society members across Belarus.
The campaign came to light recently, when a Belarus-based journalist was summoned for an “informational conversation” with the KGB. During the interrogation, officers demanded access to the journalist’s smartphone and observed the unlocking PIN. The device was returned with no visible damage, but shortly after, a warning appeared about a suspicious app. Upon further inspection by RESIDENT.NGO and RSF’s Digital Security Lab, it was confirmed that two malicious apps had been installed, one of which mimicked Adobe Reader but was in fact ResidentBat.
Targeting messaging info
Unlike advanced spyware that relies on exploiting software vulnerabilities, ResidentBat requires physical access to the target device. Investigators believe the spyware was sideloaded using Android Debug Bridge (ADB) tools after enabling Developer Mode and USB Debugging.
ResidentBat is a modular spyware family with capabilities similar to stalkerware. It abuses Android’s Accessibility Services to access sensitive data on popular encrypted messaging apps like Signal, WhatsApp, Telegram, and Viber. This allows it to capture message content as it appears on screen, bypassing end-to-end encryption. Beyond message interception, the spyware can also record calls, access SMS, internal and external storage, browser bookmarks, and even activate the microphone and camera remotely. It can wipe itself from the phone on command, erasing evidence of infection.
The spyware masquerades under names such as “Google System Service” or “OnePlus Sync Services,” and researchers identified at least eight variants with distinct package names. C2 servers linked to the malware show activity going back to March 2021, indicating a long-running and well-resourced surveillance operation.
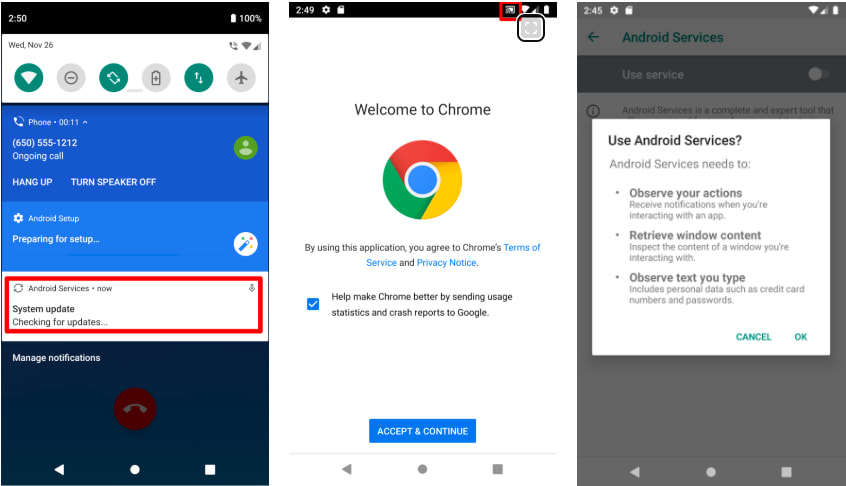
Police use of spyware
Similar tactics have been reported in Russia, where Monokle-based malware was installed on a detained activist’s phone, and in Serbia, where Cellebrite forensic tools were used to exploit Android zero-day flaws to unlock a student activist’s phone.
For those at risk, RSF and RESIDENT.NGO recommend never bringing primary devices into police stations or other high-risk locations. Instead, use secondary “burner” phones with minimal data, and ensure the device is regularly updated and protected with features such as PIN scrambling or dual-factor unlock. Devices like those running GrapheneOS or with Advanced Protection Mode offer more robust resistance to such tampering.
If a phone is out of sight while in custody, even briefly, it should be treated as compromised. Signs of infection may include unknown apps with accessibility permissions, disabled Google Play Protect, or unexplained notifications during calls or while charging. A complete forensic analysis or factory reset is advised before resuming sensitive use.
RSF has shared its findings with Google, which plans to issue threat notifications to targeted users.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


