
Researchers have demonstrated a new contactless attack technique dubbed TESLA that can recover fine-grained handwriting from smartphone touchscreens by eavesdropping on electromagnetic (EM) emissions.
TESLA (Touchscreen Electromagnetic Side-channel Leakage Attack) was developed by a team of academics from Wuhan University, Nanjing University of Aeronautics and Astronautics, the National University of Defense Technology, and Beijing University of Posts and Telecommunications. Their paper will be presented at the 61st ACM/IEEE Design Automation Conference (DAC’ 26).
How TESLA works
The vulnerability was uncovered during a study of EM side-channel emissions in capacitive touchscreens. Unlike traditional sensor-based or acoustic side-channel attacks, TESLA operates entirely passively and without device access, relying solely on EM signals unintentionally emitted during user interactions with the screen.
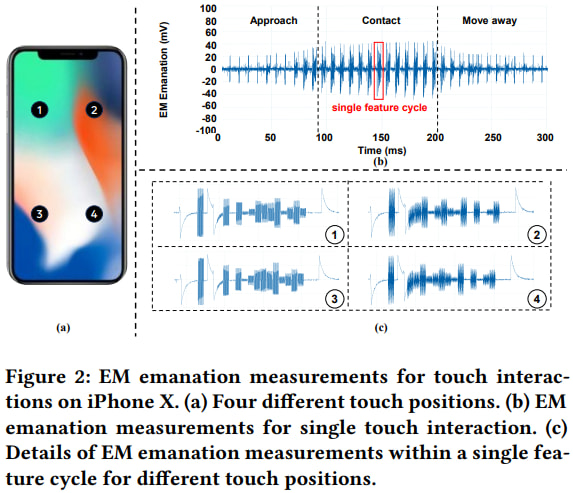
These emissions are a byproduct of how capacitive screens detect touch inputs, using a sequential Scan Driving Method (SDM) and relying on a grid of transmitting (TX) and receiving (RX) electrodes. When a user writes on the screen, the timing of these signals, modulated by the human body’s capacitive coupling, leaks subtle EM signatures that can be captured nearby.
The researchers exploited this by placing a low-cost EM probe (under $100) within 15 cm of the smartphone. The captured signal was then processed using a deep learning pipeline based on transformer neural networks that reconstructed 2D handwriting trajectories with high fidelity.
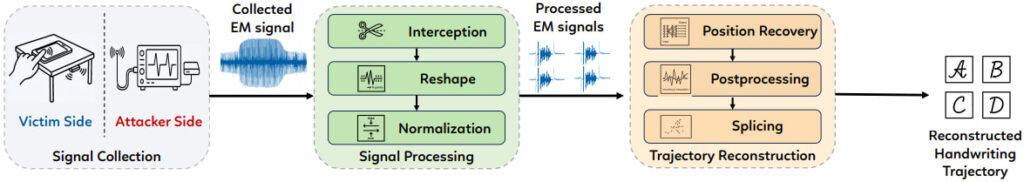
arxiv.org
The team tested TESLA across four popular commercial smartphones, namely iPhone X, Xiaomi 10 Pro, Samsung S10, and Huawei Mate 30 Pro. The system was evaluated in both quiet private settings (e.g., offices) and noisy public ones (e.g., libraries), demonstrating robust performance, with character recognition accuracy reaching 76.8%.
Recovery was even viable at distances up to 15 cm, with 73% recognition accuracy still achieved. Importantly, the attack showed consistent results across different brands and display technologies, confirming that this leakage is not a device-specific flaw but a systemic vulnerability in capacitive touchscreen design.
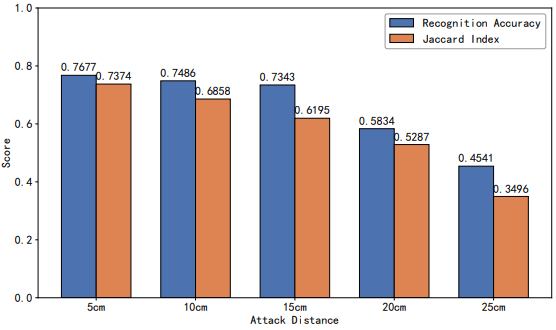
arxiv.org
The recovered trajectories aren’t just readable; they retain enough unique spatial features to potentially forge biometric signatures. The attack demonstrated effectiveness not only in extracting content (e.g., written notes) but also in impersonating handwritten authentication mechanisms such as signature verification, commonly used in financial and legal contexts.
TESLA surpasses prior methods in stealth and practicality by not requiring software installation on the target device, not making special writing style assumptions (unlike acoustic attacks), and not requiring expensive custom hardware (unlike radar-based systems). TESLA achieves this with commercial off-the-shelf probes, a discreet placement strategy (e.g., under desks or inside bags), and publicly available machine learning frameworks.
Countermeasures
The researchers warn that current smartphone designs lack sufficient EM shielding to block such attacks, and that software-level mitigations (e.g., randomizing signal timing) may not be sufficient without affecting performance.
To protect against this class of attacks, they recommend:
- Physical EM shielding in touchscreen design
- Increased hardware-level randomness in touchscreen scanning
- Security-aware placement of devices during sensitive handwriting tasks
- Awareness training for individuals in high-risk environments (e.g., signing financial documents)
Users who rely on handwriting on smartphones for any critical task should keep in mind that, without mitigations, the system remains vulnerable to passive surveillance in public and semi-private settings.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


