
The third and final day of Pwn2Own Ireland 2025 concluded with researchers demonstrating several high-impact exploits across a range of consumer and enterprise devices.
By the end of the event, a total of $1,024,750 had been awarded for 73 unique zero-day vulnerabilities, marking another successful installment of the vulnerability research competition.
Hosted by the Zero Day Initiative (ZDI) and supported by sponsors Meta, Synology, and QNAP, this year’s contest showcased cutting-edge offensive security research across devices such as smart plugs, surveillance systems, printers, IoT hubs, and smartphones.
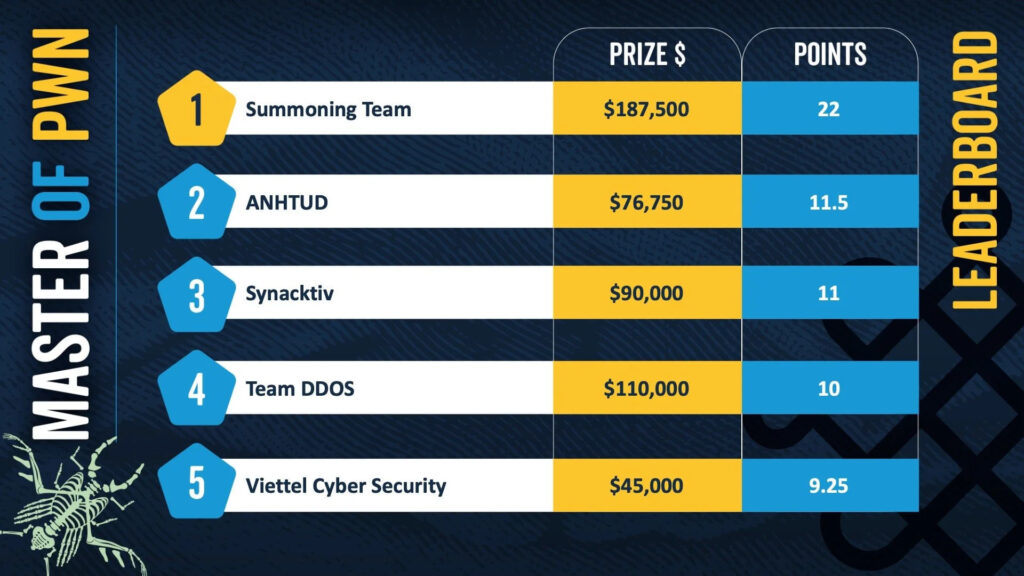
The top honors went to the Summoning Team, who claimed the Master of Pwn title after submitting several impactful and original exploits throughout the three-day competition.
ZDI
Final day highlights
Day Three saw a packed schedule of 17 remaining attempts, with both new and familiar targets under the microscope. Noteworthy successes included:
- Ben R. and Georgi G. of Interrupt Labs successfully exploited the Samsung Galaxy S25 using an improper input validation flaw, enabling access to both the camera and location tracking. Their attack earned them $50,000 and 5 Master of Pwn points, the highest payout of the day.
- Chris Anastasio of Team Cluck exploited the Lexmark CX532adwe printer via a type confusion bug, taking home $20,000 and 2 points.
- David Berard from Synacktiv executed a memorable attack on the Ubiquiti AI Pro surveillance system using a two-bug chain that included a multimedia performance of Baby Shark on the camera feed. The creative exploit brought in $30,000 and 3 points.
- Sina Kheirkhah (@SinSinology) of Summoning Team used a hardcoded credential and an injection flaw to fully compromise the QNAP TS-453E NAS, earning $20,000 and 4 points, helping secure their win.
The Philips Hue Bridge remained a popular target on the final day, but heavy overlap in exploit techniques led to multiple collisions.
- Xilokar (@Xilokar) used four bugs, including an auth bypass and underflow, to compromise the device, though one bug overlapped with a previous entry. He still earned $17,500 and 3.5 points.
- Yannik Marchand (kinnay) and Team Thalium from Thales Group both found success against the Hue Bridge but experienced similar bug collisions, slightly reducing their rewards.
Meanwhile, Team @Neodyme demonstrated an integer overflow to exploit the Canon imageCLASS MF654Cdw, earning $10,000 and 2 points, and Interrupt Labs returned with a clever combination of path traversal and untrusted search path flaws to execute code on the Lexmark printer, culminating in a reverse shell and a DOOM demo on the LCD.
If you missed the previous action in the competition, Day 1 was a record-breaking opening in the history of Pwn2Own, with over half a million awarded for 34 zero-days, while Day 2 demonstrated flaws in widely used consumer electronics like the Samsung Galaxy S25, and Philips Hue systems.
With Pwn2Own Ireland wrapped, the next chapter will take place in Tokyo, Japan, as ZDI hosts Pwn2Own Automotive from January 21–23, 2026. The focus will shift to connected vehicle systems, a growing frontier in offensive security research.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


