
Apple’s iOS 26 update introduces a change that erases a vital forensic artifact used to detect infections from Pegasus and Predator spyware, making it significantly harder for researchers and users to identify compromised iPhones.
The issue was flagged by iVerify researchers, who discovered that iOS 26 alters the behavior of the shutdown.log file, an obscure but critical log stored within Apple’s Sysdiagnose tool. Previously, this log preserved entries across device shutdowns and reboots, capturing subtle indicators of advanced spyware infections. With iOS 26, however, the log is now overwritten with each restart, effectively wiping historical evidence and removing a key source of forensic insight.
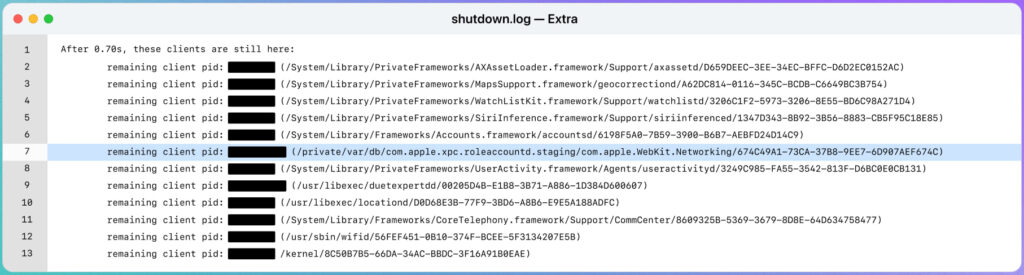
For years, the shutdown.log has served as a reliable detection point for iOS malware, including some of the most sophisticated spyware in circulation. Security researchers first noted in 2021 that Pegasus, the state-grade spyware developed by NSO Group, left behind identifiable traces in this log. By 2022, Pegasus had adapted by attempting to wipe shutdown.log, but residual anomalies still provided clues to its presence. These included sudden log truncations, missing entries, and specific file paths tied to Pegasus components. One such marker was the presence of the /private/var/db/com.apple.xpc.roleaccountd.staging/com.apple.WebKit.Networking path, indicative of Pegasus 2022 variants that had started mimicking legitimate system processes to evade detection.
Predator, another high-end spyware platform developed by Cytrox and linked to state-sponsored surveillance, adopted similar evasion tactics. Its activity within the shutdown.log also became a point of interest for forensic analysts beginning in 2023. Predator appeared to actively monitor and manipulate the shutdown logging process, likely taking cues from Pegasus’s evolving playbook.
Now, with iOS 26 automatically overwriting the shutdown.log at each reboot, this entire layer of analysis is lost. This change appears to be systemic, likely a design decision aimed at performance or system hygiene, rather than a targeted attempt to aid spyware developers. However, its timing is troubling, with high-profile spyware campaigns having escalated in recent years, targeting government critics, journalists, and other high-interest individuals.
Apple has not yet issued a statement on this issue, and it remains unclear whether the behavior is intentional or a regression. In the meantime, high-risk users should generate and securely store a sysdiagnose file from their device before updating to iOS 26. This will preserve the current shutdown.log, which could still contain critical forensic data.
If you liked this article, be sure to follow us on X/Twitter and also LinkedIn for more exclusive content.


